Today people are paranoid about data leaks as data breaches continue to get media attention. It seems now daily, just yesterday, we found out that what was reported as 320,000 people in Latitude finance is now includes almost 8 million people. So we now have the largest-known data breach of a financial institution in Australia.
Millions of Australian and New Zealand customers have had their records stolen in a cyber attack on Latitude Financial, including up to 7.9 million driver's license numbers and 53,000 passport numbers, making it the largest-known data breach on a financial institution in Australia. Today a data leak can have serious repercussions; besides harm to a company's reputation. Today there can be considerable financial losses from legal consequences. As such, people are taking strong measures to avoid such incidents.
So what happens today as computer equipment is replaced and we have the old stuff to worry about?
More than reformatting a hard drive is required to ensure confidential data cannot be retrieved. This is because of what we call data remembrance.
It is a real worry; a study from MIT here showed that data remembrance is a real threat here. In this study, 158 disk drives were purchased through eBay. 29 of the 158 drives purchased didn't work at all, and of the rest 117 (91%) of the drives contained old data that could be recovered and read. 91% is a lot.
What I found interesting is that in the sensitive information retrieved from the disk drives were detailed personal and corporate financial records, medical records, and personal e-mails such as love letters and pornography. This sort of stuff, if you go in front of a court today, could cost heaps. This is why people realise today the importance of completely erasing confidential data before disposing of hard drives.
Just reformatting a hard drive is not a secure data destruction method because of data remembrance of sensitive information. If you want to stop data remembrance, you need to either use specialised software to do a data wipe or physically destroy the hard drive.
The advantage of specialised software is that you can still have an asset, the hard drive to sell. The problem is just how good the data wipe is. Much software available today claims to permanently destroy data on the hard drive so that it cannot be retrieved or reconstructed. How good it is, I cannot say.
Now there are three options our client has. In order of security from least to best
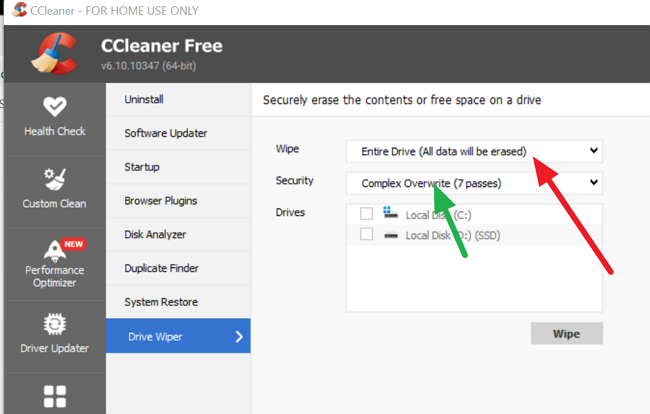
The specialised software I like which gives good results is ccleaner.
Partial clean.
Often the computer cannot be reformated as the new owner will need it to use the computer. If so, delete everything that may be a security problem. Make sure it is all your documents; some can be very embarrassing.
Then run ccleaner > disk wiper. It has the option to delete everything in free space. Select that with a complex wipe and at least three passes. That will shred everything that is deleted. If someone can crack that, they are very good at this.
Wipe the hard drive
If you can wipe the whole hard drive, go into Drive wiper and select a complex three or 7-pass wipe. On a modern hard drive, it can take a long time.
Physical destruction

Yet, more is needed by some, and they demand that we physically destroy the hard drive. The argument is that an old hard drive isn't worth much, and it is not worth the risk.
Physically destroying a is undoubtedly the most secure method to destroy its data.
If you destroy your hard drive physically, it is vital to do so correctly. A strong mallet will work. If so, I recommend putting the hard drive in a strong bag because of flying fragments before banging it. We used a canvas bag, put the hard drive in it, and smashed it. Then we put part of the remains of the hard drive in one bin and the rest of the pieces in another bin. It works well for us as two different waste disposal companies collect these bins.
Summary
> Data leaks can have serious repercussions, including financial losses and harm to a company's reputation.
> Confidential data can still be there after reformatting a hard drive due to data remembrance.
> Specialized software or physical destruction should be used
> Physically destroying a hard drive is the most secure method.


