Staff Security levels
The mere presence of you having a correct security procedures system often deters theft. If a staff member sees cameras, if they see proper procedures in the POS software, then there is less likely to be trouble. It is essential that you do take retail loss prevention seriously.
Face it if an employee sees that you won’t care about a discrepancy of a few dollars in the cash drawer, some will note this and take advantage of this. If they see a third-party your POS Software monitoring this, it will give them something to think.
One of the clients to pick up almost $13,000 a year in extra revenue when a computer system was upgraded by simply running separate tills for every staff member and introducing a policy of counting each cash drawers after each shift.
Now it is straightforward to set up in our system.
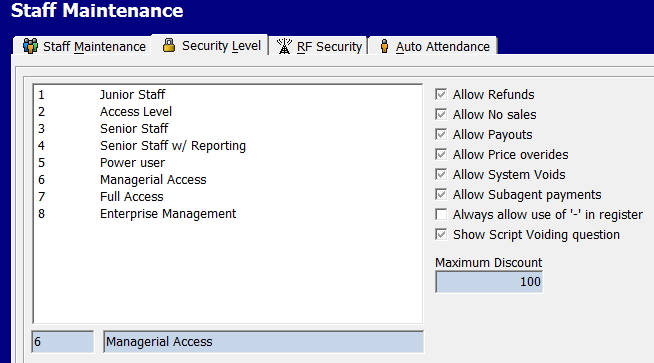
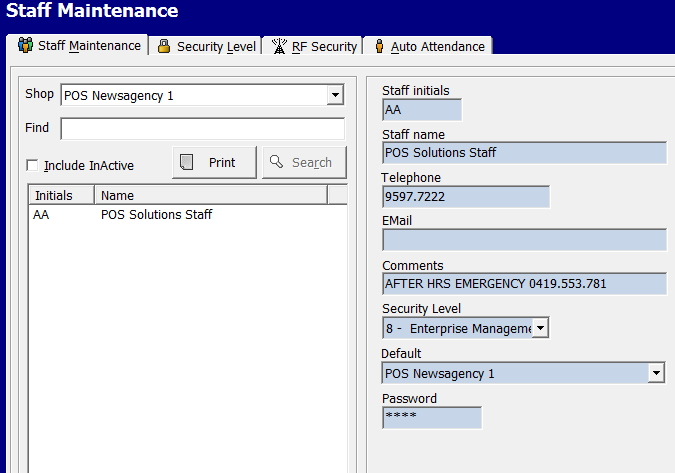
Firstly in the section "Staff maintenance", there is a section "Security Level."
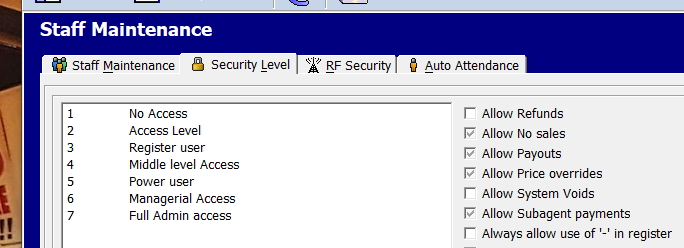
Now the defaults are there which we have set up designed to work for 90% of the shops. However, like everything, each shop is different and what works in 90% of cases often does not work with your shop so you can fine-tune it for your situation.
There are heaps as you can see options here.
Set them up for you. Now enforce them.
Now make sure you have cameras facing the tills.
Security in retail is often treated as a joke, but it does not have to be and should not be.